Over the past year, there has been a marked increase in disruptions to satellite navigation systems across the Gulf of Finland, with reports of aircraft and ships receiving false GPS signals. Evidence points to GNSS spoofing activity originating from the Russian side of the border, raising questions about its purpose and impact. While some observers see it as a form of geopolitical signaling or electronic pressure, others suggest it may be a defensive measure—intended to shield strategic areas from potential drone incursions. In this post, I will dive into what I have identified as two distinct systems of GNSS-spoofing and see what we can learn about them based on self-reported AIS positions of ships.
The Teleporting Ships
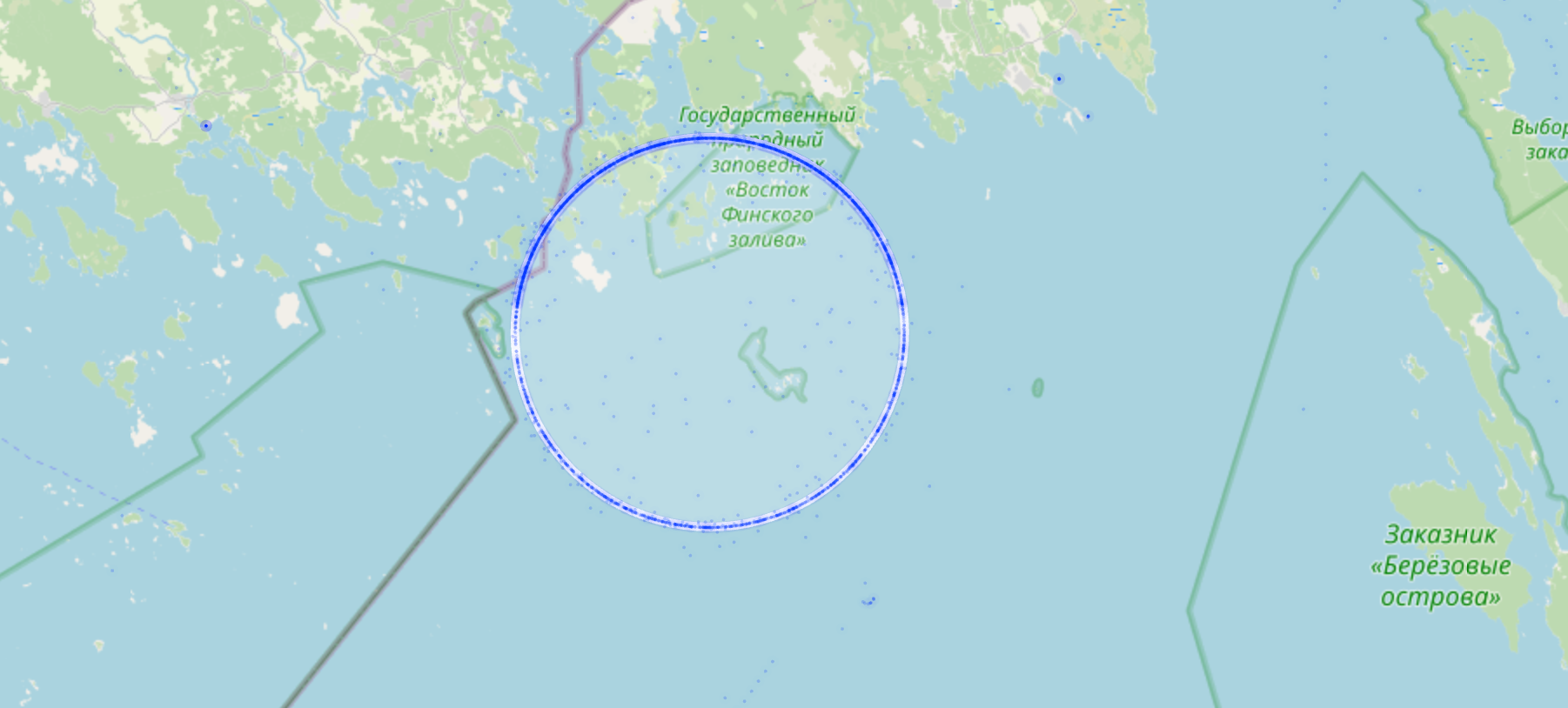
Evidence of GNSS spoofing in the area is clearly visible on ship-tracking sites such as MarineTraffic.com and VesselFinder.com. Vessels appear to follow standard shipping routes, only to suddenly ’teleport’ to a new location and begin moving in circular patterns. Ships will often drop back to their ‘real’ location, only to be caught by the spoofer once more.
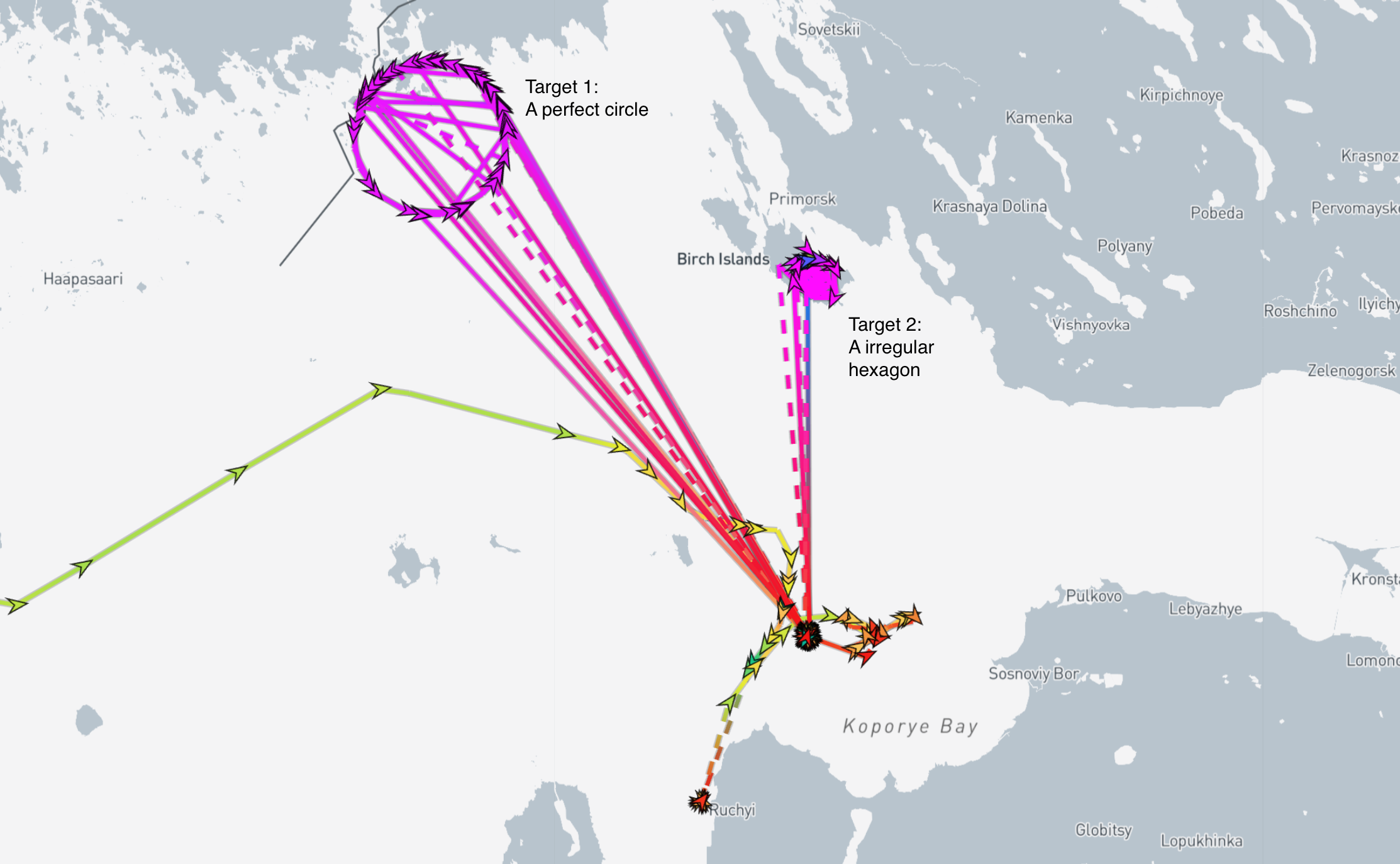
An example of such behavior can be seen above. Here, two different spoofing patterns are visible. One forming a large, near-perfect circle, and the other resembling an irregular hexagon.
It’s important to note that the spoofed target locations can be freely set by the operator, meaning the spoofed position does not indicate the actual location of the spoofer. In this case, the false positions appear to be in areas with no obvious military significance.
The Great Circle-Spoofer
The first system I will dive into is the circle-spoofer. Converting the coordinates of ship traffic in the region to a metric coordinate system, reveals a perfect circle with a radius of 8.6 km centered on N 60° 25’ 27 E 27° 52’ 48. This was found using the Taubin circle-fitting method.
After this, it is trivial to normalize the circle and transform it into polar coordinates, as seen below.
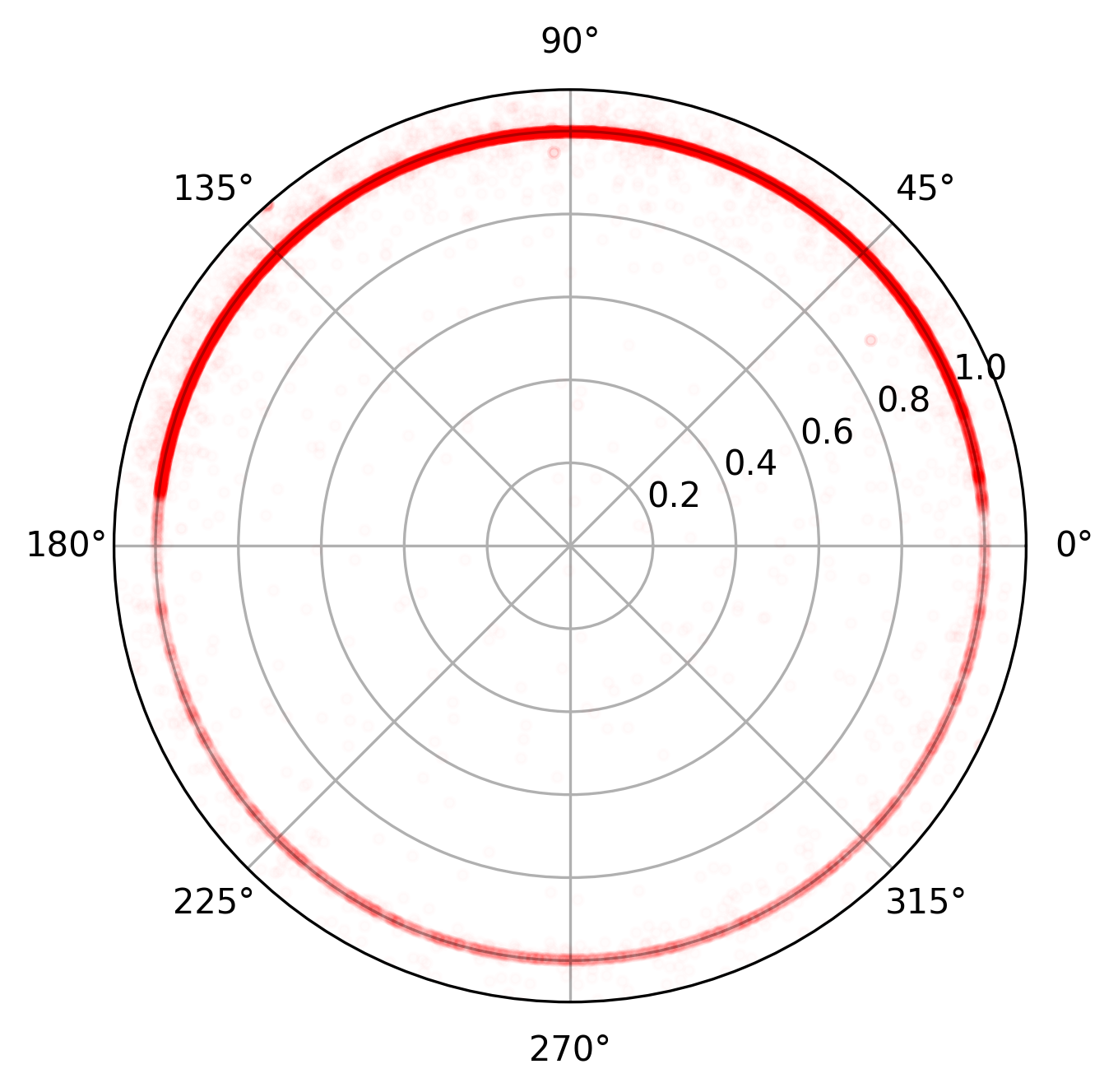
From the polar plot, it’s evident that the upper half (0–180 degrees) contains significantly more data points than the lower half. This suggests that the spoofer may be operating in multiple modes.
When taking the timestamps of the observed AIS positions into account, it becomes clear that the circle-spoofer outputs a single point on the circle at any given moment. This means that if two ships are within range of the spoofing signal at the same time, they would appear to occupy the exact same position.
This behavior becomes apparent when plotting the angle over time (high-res version):
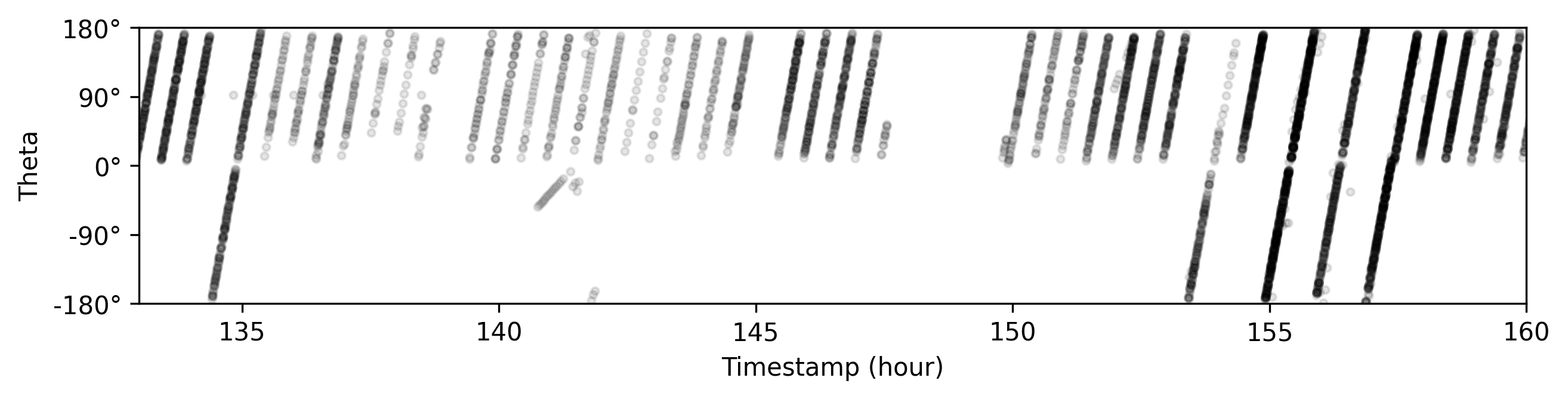
Analysis of the plot above reveals that the spoofer operates in either half-circle or full-circle mode. The half-circle mode has a period of 30 minutes, while the full-circle mode, as expected, completes a rotation in 60 minutes. There is no clear pattern or identifiable trigger for when or why the system switches between these two modes.
By wrapping the time axis at one-hour intervals, additional details about the spoofer’s operating mode become visible:
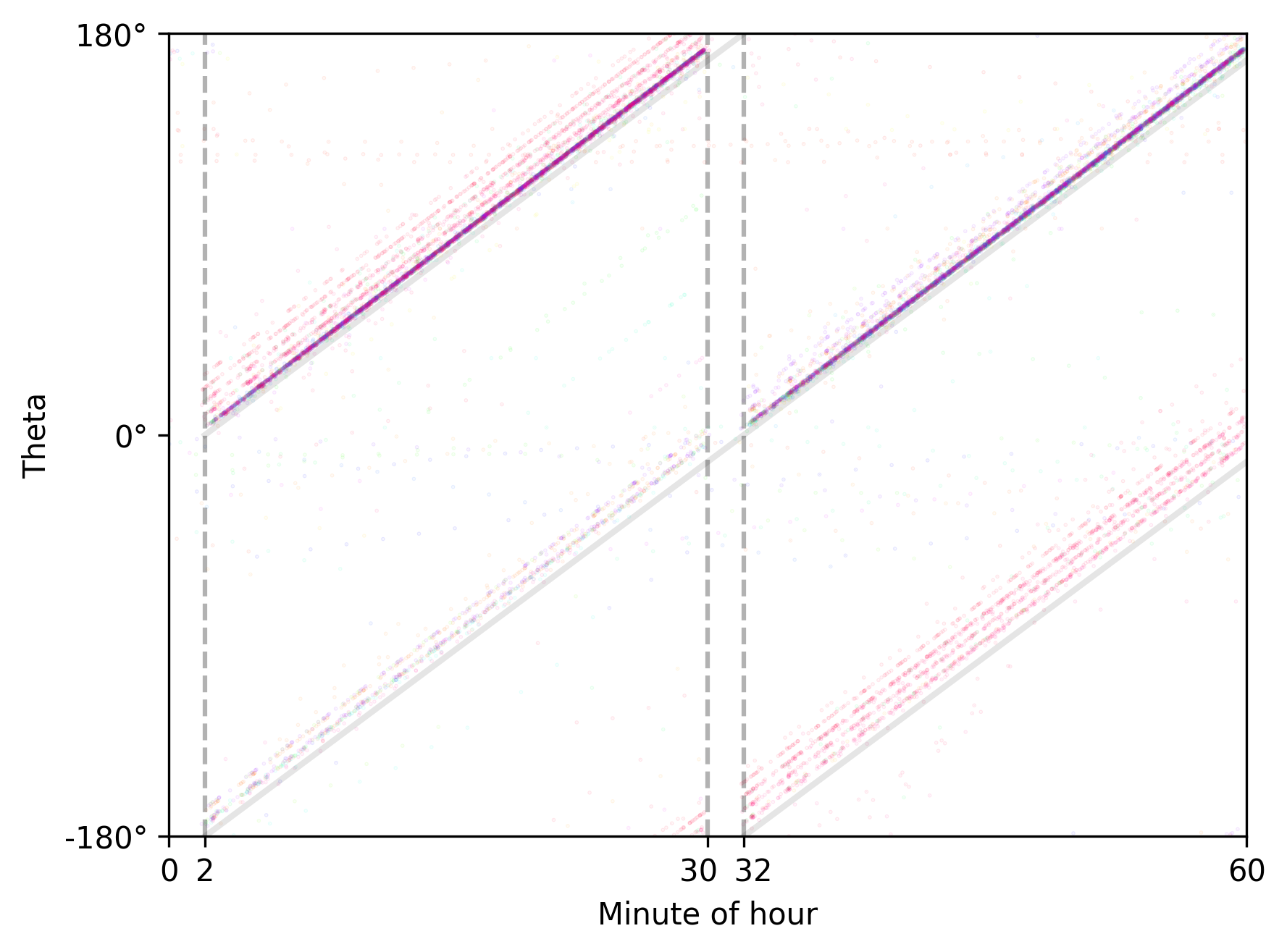
First, we observe that the spoofer is inactive for two brief periods—each lasting approximately two minutes—at the top and bottom of every hour. This behavior occurs regardless of whether it is operating in half-circle or full-circle mode. It’s a useful detail to keep in mind: if you ever encounter this type of circle-spoofer in the real world, your GNSS position is most likely accurate around the start and end of each hour.
Secondly, a few of the lines appear to be out of phase. This may indicate clock drift within the spoofing system, and the effect seems to be more pronounced when it operates in full-circle mode.
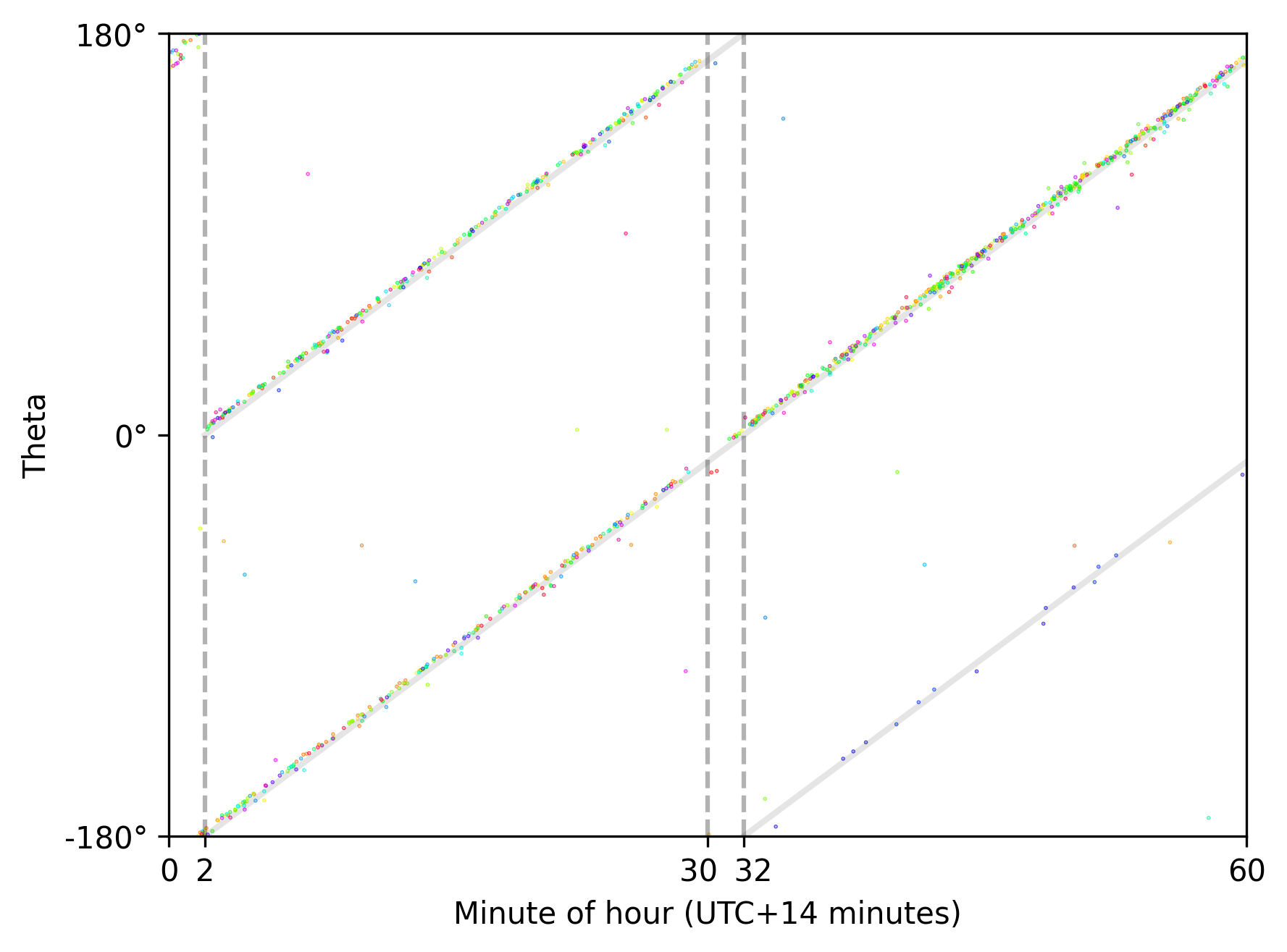
Interestingly, a similar behavior can be seen for the “Null Island” target spoofer, which was deployed near Novorossiysk in March 2025 (thanks @claudialanz). Here the spoofed location consistenty alternates between following one 60-minute and two 30-minute scan patterns (offset by 15 minutes from UTC, approximately):
The Little Croocked Hexagon
As with the circle-spoofer, the line-based spoofer broadcasts a single spoofed position at any given moment, shared by all GNSS receivers within its range.
Its target location is on an island just off the coast of Primorsk. The spoofed position pattern appears to be loosely hand-drawn—the lines overlap slightly and follow the island’s general shape.
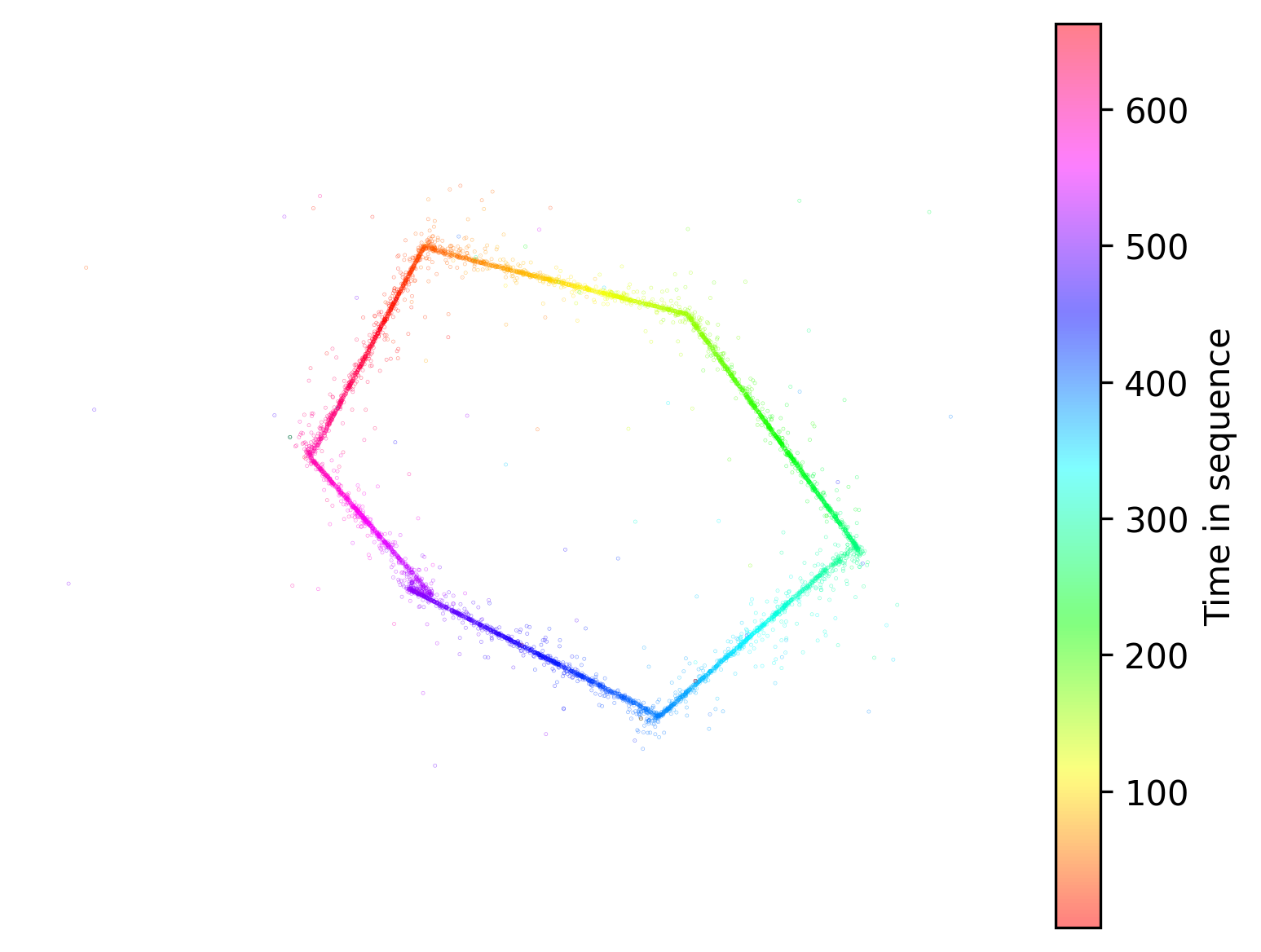
The position pattern repeats every 662.84 seconds, but unlike the circle-spoofer, this system broadcasts continuously with no observable breaks.
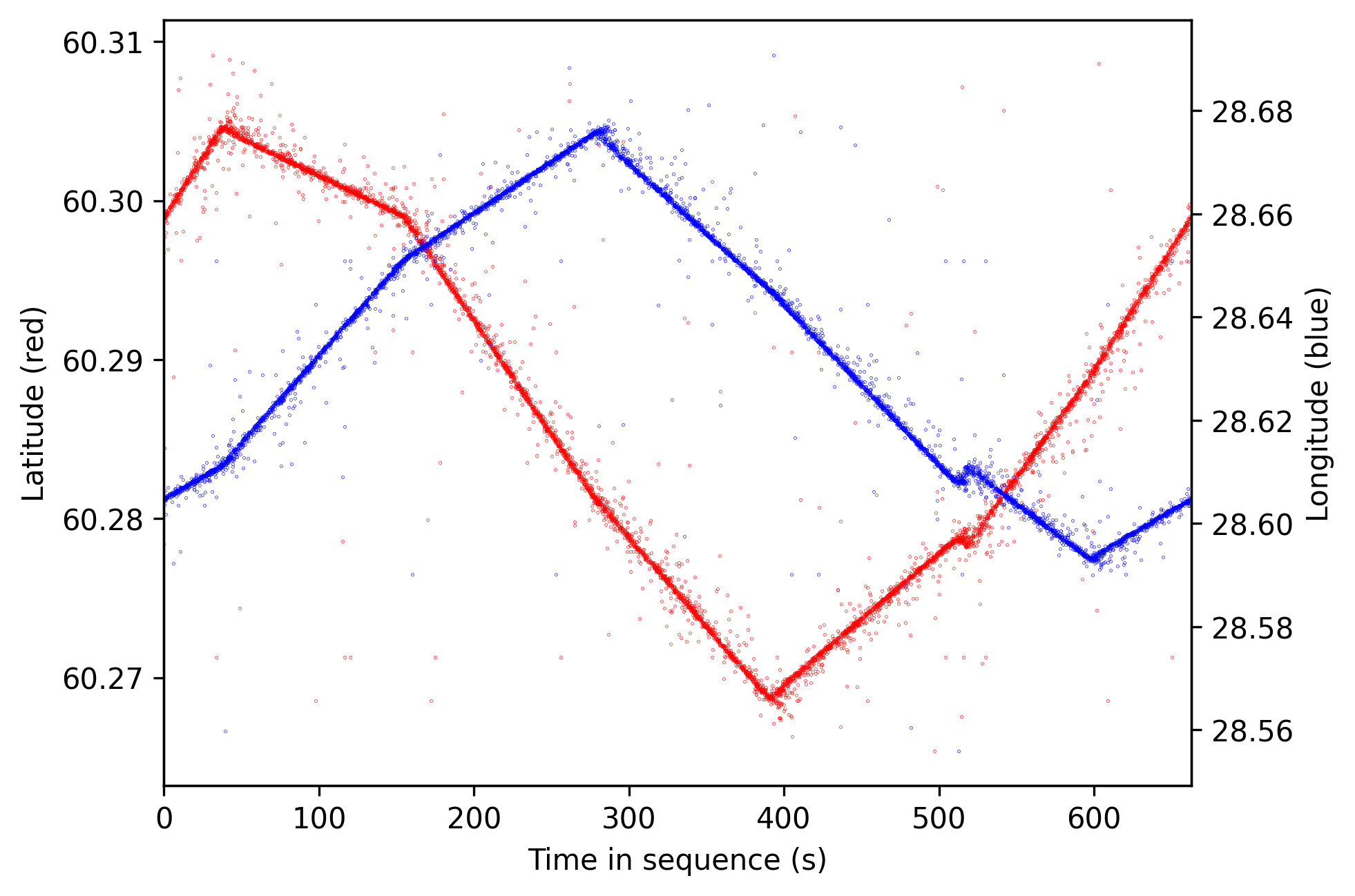
Determining the repetition period for this spoofer was more challenging, as it had to be visually estimated by adjusting the scan duration.
So, What Can We Learn?
Both spoofing systems — the circle and the line variants — could theoretically be synchronized across a fleet of similar devices. All observations suggest that the phase of the spoofed output is aligned with universal time (UTC), implying some degree of clock synchronization.
However, certain behaviors hint that each spoofer might be an individual, standalone deployment.
For the circle-spoofer, the seemingly random switching between half-circle and full-circle modes would require coordination across all units, which is technically feasible but unnecessarily complex. It would be far simpler to keep each spoofer in a fixed operating mode.
The line-spoofer adds further weight to this idea, as it goes offline for long periods and seems focused on affecting ships near Primorsk specifically.
I also attempted to determine whether the spoofers were mobile or stationary. While I couldn’t draw a definitive conclusion, I lean toward them being mobile systems — especially in the case of the circle-spoofer — due to the wide area it affects.
Achieving such coverage with fixed installations would be difficult, considering line-of-sight constraints and signal loss over distance.